Advisory from the ECPI University Cyber Center for Innovation
The WannaCrypt ransomware worm, aka WanaCrypt or Wcry, was released on Friday May 12th, 2017. It has spread to at least 150 countries, infecting hospitals, businesses including Fedex, rail stations, universities, at least one national telco in the UK and many more organizations. Making this one of the biggest malware attacks in recent history.
Ransomware prevents users from accessing their computers, files, or mobile devices by holding them for ransom. Users are typically expected to pay high ransom amounts to get access back to their data. Many times the ransomware will falsely claim that the user has committed a crime with their computer, and that they are being fined by the police department or a government agency.
Details About the WannaCrypt Ransomware Infection
WannaCrypt is installed on vulnerable Windows computers by a worm that spreads across networks by exploiting a vulnerability in Microsoft’s SMB file-sharing services. It specifically abuses a bug designated MS17-010 that Microsoft patched in March for modern versions of Windows. Microsoft has also released emergency security patches to defend against the malware for unsupported versions of Windows, such as XP and Server 2003.
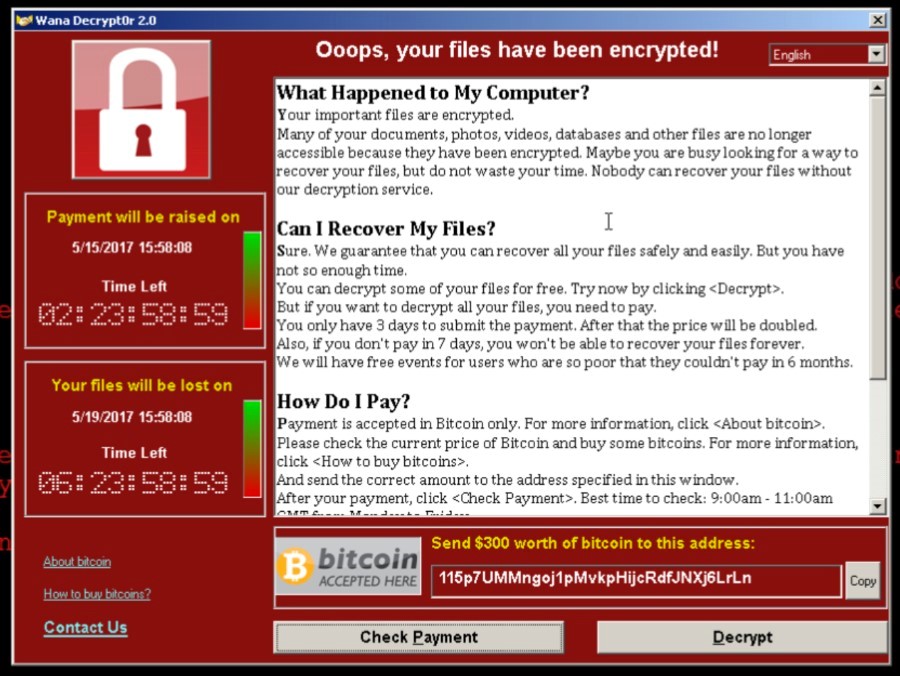
Screenshot of WannaCrypt Ransomware
Personal Prevention: How to Keep Devices Safe
Anyone is susceptible to this type of malware. One key thing to do is to back up your important files to an offline drive. This mitigates the risk of ransomware by bypassing the tool it uses to get victims to pay a ransom.
Ransomware can be avoided by practicing the following safe browsing and email habits:
- Never respond to spam emails.
- Open only known or expected attachments.
- Do not click on links in emails. Always copy and paste links to a browser.
- Avoid using your email account to register for random or short-term services.
For your personal Windows devices, Microsoft offers advice on how to keep them safe and deal with issues that may arise. You can also obtain a patch for any Windows XP devices if you need to.






