Bad Rabbit Advisory from the ECPI University Center of Excellence
Networks in Russia and Eastern Europe were targeted by a new strain of ransomware named ‘Bad Rabbit,’ a possible variant of the ‘Petya’ malware that hit computer systems earlier this year.
Bad Rabbit, which originated in Ukraine, was first seen on computers at the Odessa international airport in southern Ukraine and the Kiev subway. Russian media outlets such as Interfax and Fontanka also reported being targeted this past Tuesday. Security experts have said that the malware was also detected in Poland and South Korea.
The malware is spreading through compromised websites, presenting itself as an Adobe Flash Player download.
Technical Details Surrounding the Latest Ransomware Attack
Research suggests that the ransomware worm used a stolen Equation Group exploit revealed by Shadowbrokers to spread across victims’ networks. The attackers used EternalRomance, enabling remote execution of instructions on Windows clients and servers. The code uses an open source Python implementation of a Windows exploit that used EternalRomance (and another Equation Group tool, EternalSynergy), using the same means seen before in the Shadowbrokers code release. Petya used this exploit as well.
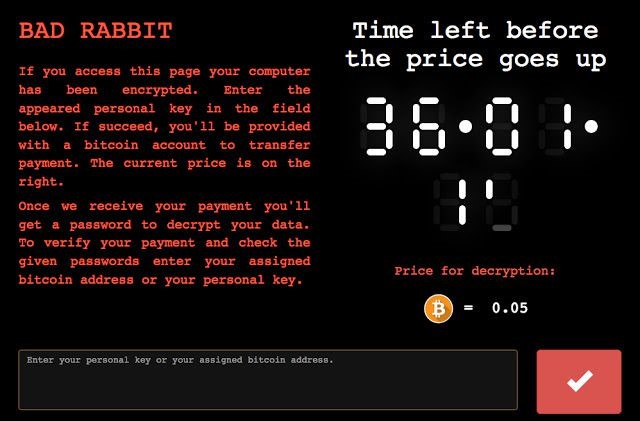
Once infected with the ransomware, victims are directed to a web page on the dark web, which demands they pay 0.05 bitcoin (roughly $285 USD) to get their files back.
After one computer on a network is infected, Bad Rabbit can quickly spread through an organization’s network without being detected. Although the ransomware has been detected in several countries, it appears to be concentrated in organizations in Russia and Ukraine, particularly media outlets.
Presently, it is still unknown who is behind the dissemination of the Bad Rabbit ransomware. Nevertheless, its likeness with Petya gave experts reason to believe that the perpetrators behind the Petya attack are the same as those behind Bad Rabbit.
This case is puzzling security researchers because of the fact that the attackers also hit Russia which was believed previously to be the source of the Petya attack.
Recommendations for Avoiding the Damage Caused by Bad Rabbit
The US computer emergency readiness team said it “discourages individuals and organizations from paying the ransom, as this does not guarantee that access will be restored”.
At the time of this writing, quite a few security vendors state that their products protect against Bad Rabbit. But for those who want to be sure they don’t potentially fall victim to the attack, Kaspersky Lab recommends that users block the execution of file ‘c: \ windows \ infpub.dat, C: \ Windows \ cscc.dat.’ in order to prevent infection.
At the end of the day, all ransomware is essentially the same. Users can mitigate the impact of ransomware in general with the following best practices:
- Regularly backup your files
- Keep your programs and operating system updated
- Enforce the principle of least privilege
- Disable unnecessary and outdated services and programs
- Make sure to always have the latest antivirus updates on your Antivirus solution of choice
- Be wary of emails that are unexpected and suspicious, especially if they contain attachments or links


