By Dr. Walter Brock, PhD, CIS Faculty Greenville
If you have been in IT for any period of time, you know the rules for good passwords by heart right?
Is this a good password?
P1a$$W0rD!
Well, let’s see:
- It has more than 8 characters.
- It contains 2 numbers, 2 capital letters, 2 lower case letters, and 3 special characters.
- One of the characters has been put in a place as an attempt to “mess up” a dictionary-based attempt at deciphering it.
Even with all of these characteristics, I’m sure most people reading this would agree that it is NOT a good password. In fact, many of the passwords we use these days as login credentials are just as bad. Or, so says Bill Burr who actually wrote the book (NIST Special Publication 800-63, Appendix A) on passwords back in 2003.
The problem? Well, there are several. First off, when Mr. Burr wrote those rules in 2003, there was very little research or empirical evidence to guide him. In fact, he reports that his superiors actually scoffed at him when he asked for that information. Now, 14 years later, we have that research and the evidence. It turns out, the original rules don’t hold up against the research. All the rules about numbers, letters, and special characters are, according to Mr. Burr, a waste of time.
One simple animation that appeared on the XKCD web site explains the problems in rather concise fashion:
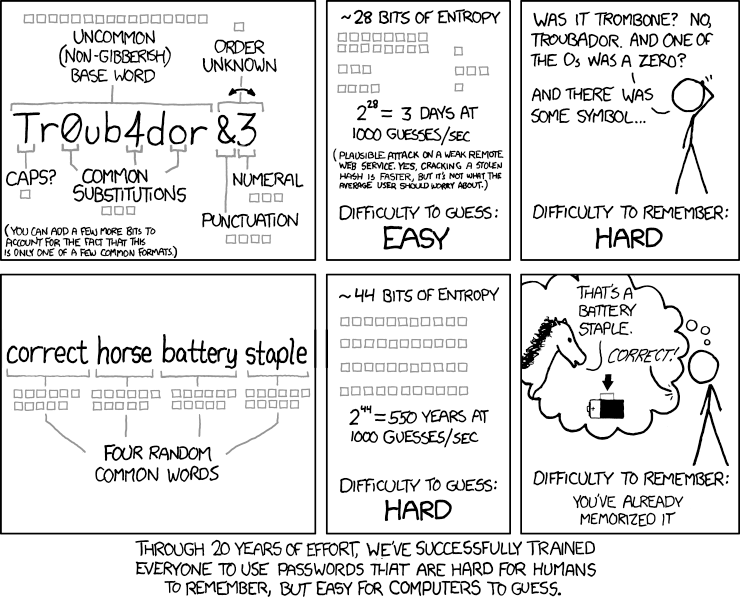
Source: https://imgs.xkcd.com/comics/password_strength.png – Released under the Creative Commons License.
If we are to believe the pundits and the researchers, then the long passphrase is far superior to the old password. There are a couple caveats here. First, the passphrase has to be long enough (note, the example of 4 words). Second, the words in the passphrase must be random – “ilovemymom” is both shorter and less random than the example above.
A new version of NIST Special Publication 800-63 was released in June of this year. The majority of the old password rules have been deleted from this new version.
In the meantime, we still have the old password rules built into or embedded in just about every server operating system and password policy in existence. So, do we start changing our systems whole scale and retraining our users? Or do we stick with what we think we know? For those of us who have been in IT for many years, some of this is a little hard to swallow.
One last question: If we let our users pick long, but easily remembered pass phrases, will they still write them on Post-It notes?
Anyone up for two factor authentication?



